HTTPS Configuration
This guideline will show you on how to run Ambience 4.x in HTTPS mode using a self-signed certificate and this can be done by using openSSL keystore.
Prerequisites: Verify that OpenSSL installed on the system. For windows you can get it from Win32/Win64 OpenSSL Installer for Windows - Shining Light Productions
1/ Below are the three files that need to be add in your “jetty\elx-base\etc” path of your Ambience directory.
- jetty-https.xml
- jetty-ssl.xml
- jetty-ssl-context.xml
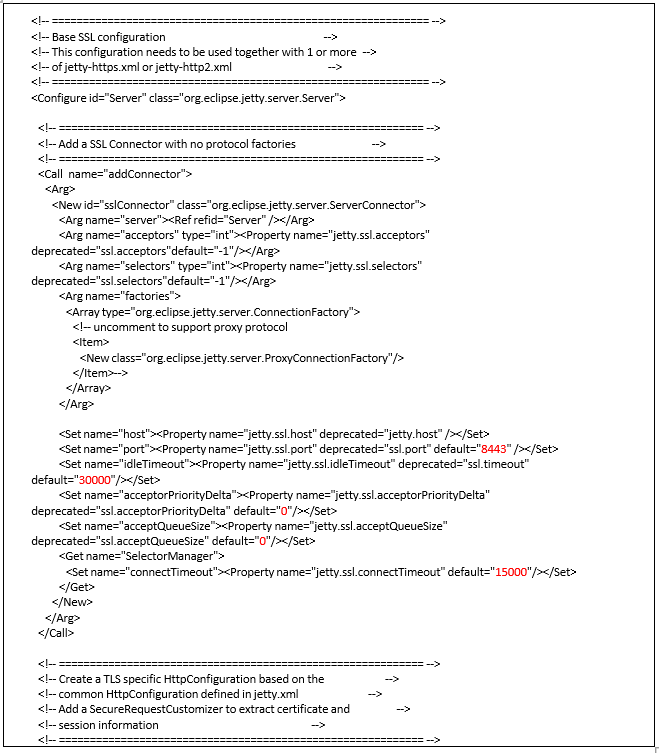
jetty-https.xml
jetty-ssl.xml
Note : Please update the value below (as above highlighted in red).
1/ ssl port default
2/ ssl timeout default
3/ ssl acceptor priority delta default
4/ ssl accept queue size default
5/ ssl connection timeout default.
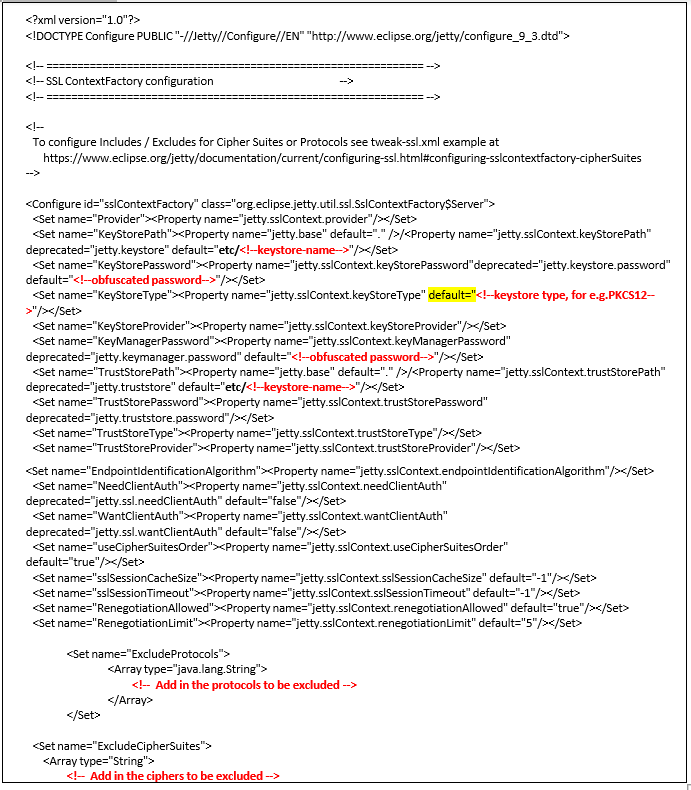
jetty-ssl-context.xml

Note : Please update the keystore name (more information on the next step), keystore type e.g in this case we are using PKCS12 and obfuscated password
For more information about the obfuscated password, please refer to this link (Page 27)
Create a Private Key / Certificate Signing Request / Self-Signed Certificate and Keystore
Creating a Private Key
First, we’ll create a private key. A private key helps to enable encryption and is the most important component of our certificate.
openssl genrsa -des3 -out server.key 2048
Creating a Certificate Signing Request
If we want our certificate signed, we need a certificate signing request (CSR). The CSR includes the public key and some additional information (such as organization and country).
Create a CSR (server.csr) from our existing private key:
openssl req -new -key server.key -out server.csr
Creating a Self-Signed Certificate
A self-signed certificate is a certificate that’s signed with its own private key. It can be used to encrypt data just as well as CA-signed certificates, but our users will be shown a warning that says the certificate isn’t trusted.
Create a self-signed certificate (server.crt) with our existing private key and CSR:
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
note: The -days option specifies the number of days that the certificate will be valid.
Create a PKCS12 keystore from a private key and certificate.
The private key and certificate must be in Privacy Enhanced Mail (PEM) format. Use the following OpenSSL commands to create a PKCS#12 file from your private key and certificate
- Open terminal.
- Execute the following commands.
note : Make sure that the following commands are executed at the same directory in where “server.key” and “server.crt” resides.
Create a PEM file.
Unix/Linux Command
cat server.key > server.pem
cat server.crt >> server.pem
Windows Command
type server.key > server.pem
type server.crt >> server.pem
Create .pkcs12 file
openssl pkcs12 -export -in server.pem -out keystore.pkcs12
Once keystore generated please copy over to jetty/elx-base/etc path of your Ambience installation.
Edit the start.ini file found in your “jetty\elx-base” directory and add in below following lines:
● Under the following comment, “# Module: http”:

Start up your Ambience server. Open browser and verified the HTTPS port protocol.
For example, https://localhost:8443
Below was the full documentation and the jetty xml files:-
HTTPS Configuration Ambience 4.pdf (204.7 KB)
jetty-xml files.zip (2.4 KB)