How To Enable X-Frame Options Header To Disable ClickJacking in Repertoire 8.9 and Above
In this post, I’ll share how to set up an appropriate X-Frame-Options or Content-Security-Policy HTTP header in Repertoire 8.9 and above.
This will prevent attackers from “hijacking” clicks meant for login and stealing their credentials.
In this example, we are using Burp Suite Community Edition and Burp ClickBandit to demonstrate how to identify Clickjacking Vulnerabilities and to configure accordingly.
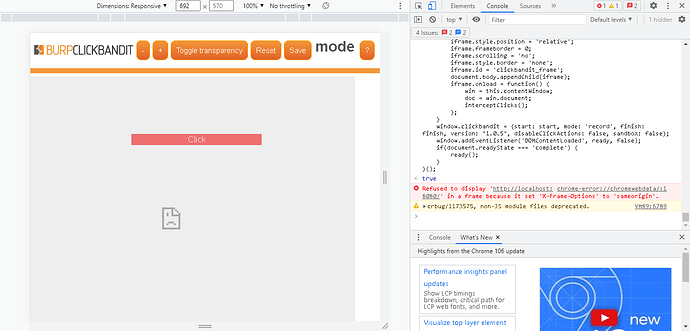
Step 1: Identify Potential ClickJacking With Burp ClickBandit
-
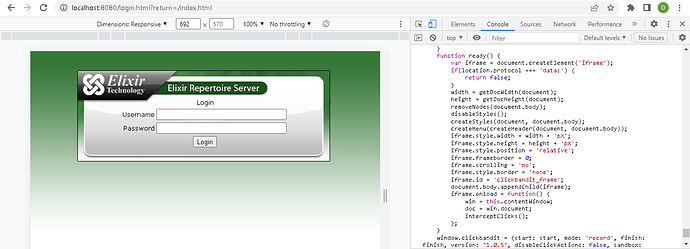
Visit the page you would like to test.
-
Press F12 to open the web developer console.
-
Open ClickBandit_JavaScript.txt. Copy and paste the codes in the console of your browser.
Step 2: Run The Attack As Instructed
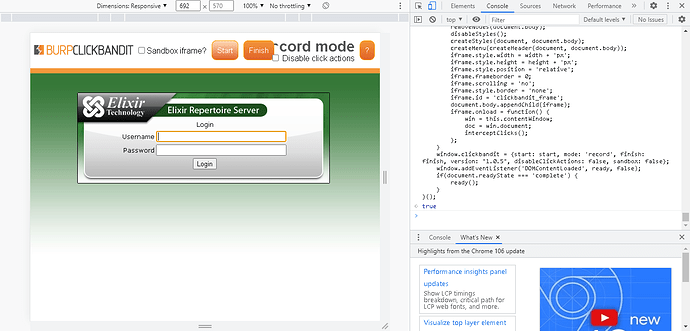
- Click the start button to start. For testing purposes, we just click anywhere in the page.
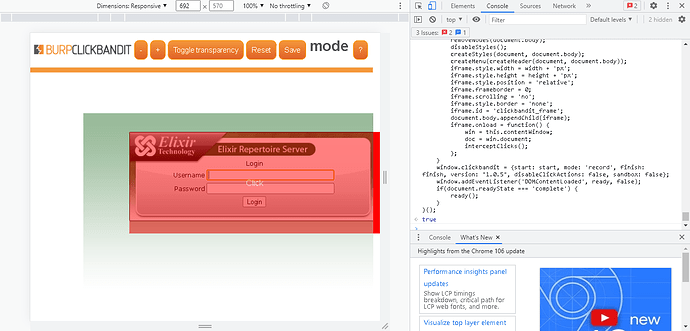
- Once you are done, click the finish button to end.
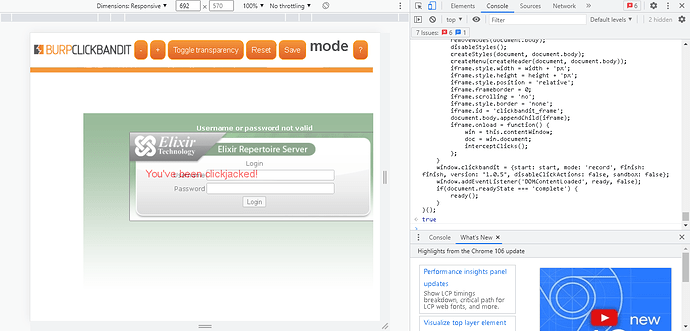
- Click anywhere in the page to trigger the attack. You should be able to see the message “you’ve been clickjacked”.
Step 3: Enable X-Frame-Options HTTP Header Field
-
Open ERS2.xml in the Repertoire Server directory. It can be found under the sub folder config.
-
Remove the comment for the following codes from line 172 onwards to this:
<ers:property name=“XFrameOptionFilter”>SAMEORIGIN</ers:property>
<ers:property name=“StrictTransportSecurity”></ers:property>
- Save the file and restart the server.
Step 4: Execute the Above Sequence Again
- You should be able to see the following result.
Resource:
https://www.invicti.com/web-vulnerability-scanner/vulnerabilities/missing-x-frame-options-header/
https://portswigger.net/support/using-burp-to-find-clickjacking-vulnerabilities
Clickbandit_JavaScript.txt (30.4 KB)