Traditional Approach
Previously, connection pools were typically defined in the application.conf file, as shown below:
elixir.data.jdbc.connection-pool {
definition {
mysql = "./etc/mssql.properties"
}
}
Reference: Creating a MSSQL JDBC connection pool
Alternative Approach: Inline Connection Pool Definitions
1. Download the sqldbc Driver:
Obtain the appropriate sqldbc driver for your database. Place the driver file into the /lib or /ext directory of the Ambience 202x installation.
2. Include new configuration line in application.conf
Ensure that the following line is added to the application.conf file. This step ensures that configurations made in the Config Editor module are correctly loaded upon server restart:
ambience.config-loader.mongodb.enabled = true
3. Start the Ambience Server:
Launch the Ambience server to ensure all necessary services are running.
4. Log into Ambience:
Access the Ambience interface using your credentials.
5. Navigate to the Config Editor:
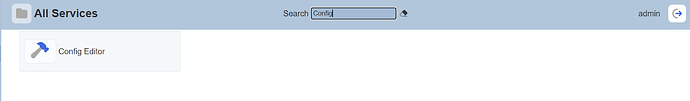
In the left panel, click on ‘All Services’.
Use the search bar to locate ‘Config Editor’ and select it.
5. Define the Connection Pool Inline:
In the Config Editor, modify or add the relevant configuration for the connection pool as follows:
The updated configuration can be managed through the Config Editor module in the web interface, eliminating the need for on-disk file access.
6. Apply Changes and Restart
After saving the changes in the Config Editor, restart the Ambience server to apply the updated connection pool configuration. Connection pools are initialized during server startup, so a restart is mandatory for changes to take effect.
Key Rules:
1. String Values Indicate File References :
If the value is defined as a string (e.g., mysql = “/path/to/hikari.properties”), it references a file on disk.
2. Nested Objects Are Inline Configurations :
If the value is a nested object (e.g., mysql = { … }), the configuration is read directly from the nested config.
3. HOCON Syntax Compliance :
Inline configurations must adhere to HOCON (.conf file) syntax rules. For example, strings must be quoted (e.g., “52816”). Hikari treats all values as strings, so “52816” and 52816 are treated equivalently.
4. Enhanced Security with {secret} Syntax :
Secrets can be referenced using {secret}XXX, which pulls the value from the Secrets module for the secret named XXX. This syntax is now supported both in inline configurations and Hikari files on disk. Additionally, {enc:…} encoding is available for secure storage of sensitive data.
5. Cluster-Wide Synchronization :
Defining connection pools in config ensures consistency across all servers in a cluster. There’s no need to synchronize Hikari property files manually.
6. Restart Required for Changes :
Connection pool configurations are only applied upon server restart. This prevents potential risks associated with modifying connection pools while reports or other operations are in progress.
Benefits of the New Approach
1. Simplified Deployment : Eliminates the need for external file management, making it easier to configure Dockerized containers without volume mounts.
2. Web-Based Configuration : Users can modify connection pool settings directly through the Config Editor module, streamlining administrative tasks.
3. Improved Security : Sensitive data, such as passwords, can be securely managed using the {secret} syntax integrated with the Secrets module.
4. Cluster-Wide Consistency : Ensures all nodes in a cluster use the same configuration without requiring manual synchronization of files.
Availability
This feature is included in the A2025 series.